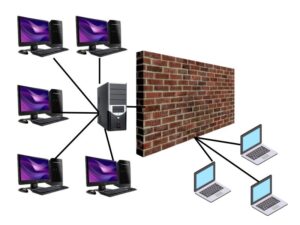
As the world’s reliance on technology grows, network security has become an essential component of securing sensitive data and deterring cyber assaults. The Role of firewalls in network security cannot be emphasized. Data breaches may have severe effects on individuals, businesses, and organizations of all kinds in today’s digital era. Network security refers to all of the procedures required to safeguard a network from unauthorized access, theft, and data loss.
The firewall is a crucial component of network security. Firewalls serve as a barrier between a network and the outside world. They aid in the prevention of unauthorized network access and may be set to allow or block particular types of traffic depending on criteria such as port numbers, IP addresses, protocols, and applications.
Dear friends, In this article, we will learn what is the role of firewalls in network security and going to examine why they are critical for our network security. We’ll look at the many types of firewalls and their filtering techniques, as well as the significance of firewall rules in setting a firewall to give the greatest possible protection against cyber threats.
What is a Firewall?
A firewall is an important network security device that helps to defend a network from cyber-attacks. It is a software program or hardware device that stands between a company’s internal network and the internet, analyzing incoming and outgoing network traffic and choosing whether to allow or block certain data depending on predefined security criteria.
Role of Firewalls in Network Security
A firewall’s principal role is to prevent unauthorized network access by blocking malicious traffic while allowing legal traffic to get through. It accomplishes this by inspecting and comparing each incoming and outgoing network packet to a set of predetermined rules. If the packet fits the conditions of the rule, the firewall will let it through. If the packet does not satisfy the requirements, the firewall will reject it, preventing the network from being hacked.
To assess whether traffic is allowed or banned, firewalls can be configured to employ a variety of different filtering methods. Packet filtering, Stateful inspection, and application layer filtering are examples of these. Individual data packets are examined and either blocked or allowed based on information such as the packet’s source and destination IP addresses, port numbers, and protocol. In contrast, Stateful inspection evaluates the context of the communication to identify whether a packet is part of an established connection. Application layer filtering analyses packet contents and can either block or allow traffic based on the kind of application delivering the data.
Firewalls can be configured to fulfil additional key network security duties in addition to blocking or accepting network traffic. They can, for example, track and alert network managers to questionable activities, check incoming and outgoing emails for viruses and malware and offer remote employees virtual private network (VPN) access.
Firewalls play an important role in network security by acting as a strong line of defence against cyber-attacks. Firewalls assist in preventing unauthorized network access and secure sensitive data by analyzing incoming and outgoing traffic and implementing security rules. The next sections will go through the various types of firewalls and their filtering methods, as well as how to create firewall rules for optimal protection.
Types of Firewalls
There are several types of firewalls, including:
- Packet Filtering Firewalls: Packet Filtering firewalls analyze incoming and outgoing packets and allow or deny traffic based on criteria such as source and destination IP addresses, port numbers, and protocols. This is the most basic sort of firewall since it just analyses packets for information that is already provided in the packet header. These firewalls are fast and efficient, but they provide limited security.
- Stateful inspection firewalls: Stateful inspection firewalls monitor the status of connections and use this information to determine whether to allow or prohibit traffic. Stateful inspection firewalls, as opposed to packet filtering firewalls, examine the context of each packet as well as the interaction between packets in a connection. As a result, they are more secure than packet-filtering firewalls.
- Proxy Firewalls: Proxy firewalls operate as go-betweens for the user and the internet. They receive user requests and send them on their behalf, offering an additional layer of security by hiding the user’s IP address. Proxy firewalls also provide more granular control over the traffic that enters and exits a network.
- Next-Generation Firewalls: Next-Generation firewalls combine the best aspects of the three types of firewalls outlined above. To provide improved security, they employ current techniques such as deep packet inspection, intrusion prevention, and antivirus. Because of their capacity to identify and stop complex assaults, these firewalls are becoming an increasingly attractive alternative for organizations trying to safeguard their networks.
Because each form of firewall has unique strengths and drawbacks, it is critical to select the appropriate type of firewall depending on your organization’s specific needs. A network security specialist can assist you in determining which sort of firewall is most suited to your organization’s requirements.
In the next section, we’ll look more closely at some of the characteristics and functions of firewalls.
Why Are Firewalls Essential for Network Security?
Firewalls have evolved into an essential component of network security, and their significance cannot be emphasized. Here are some of the reasons why firewalls are so important for network security:
- Malware Protection: Firewalls prevent malware from entering the network by blocking traffic from known malicious IP addresses and domains. Using advanced threat intelligence and analysis, they can also detect and prevent malware disguised in network traffic.
- Prevent Unauthorized Access: Firewalls protect sensitive data from unauthorized access by preventing unauthorized access attempts. They may verify users before granting them network access, as well as monitor user activities to detect any suspicious behaviour.
- Govern Network Traffic: Firewalls add another layer of security by allowing administrators to govern network traffic by blocking specific ports and protocols. They can also limit bandwidth use to avoid network congestion, which can aid in network performance optimization.
- Compliance: Many regulatory laws require organizations to construct a firewall to protect sensitive data. It is vital to follow these guidelines in order to avoid fines and other consequences.
- IoT Device Protection: With the growth of the Internet of Things (IoT), firewalls have become more crucial than ever. Firewalls can help safeguard IoT devices by restricting unauthorized access and monitoring network traffic.
Best Practices for Firewall Configuration
While firewalls are an important component of network security, they are only effective if properly set. Here are some firewall-setting best practices:
- Establish Security Policies: A critical stage in efficient firewall configuration is the establishment of security policies. Security policies should be developed with a clear knowledge of the organization’s business requirements, such as which traffic should be allowed and which traffic should be limited. This data may be used to set up the firewall’s rules.
- Regularly Update Firewall Rules: Firewall rules must be kept up to date in order to handle emerging threats and preserve the firewall’s effectiveness. This necessitates routine audits of firewall rules and configurations. Firewall rules should also be updated to reflect changes in the network architecture of the organization, such as new apps, devices, or network connections.
- Use Multiple Security Layers: Firewalls are an important aspect of network security, but they should be used in conjunction with other security measures to offer several levels of defense. Antivirus software, intrusion detection and prevention systems, and web filtering are examples of additional security layers. Using many levels of security reduces the likelihood of a security breach.
- Monitor Firewall Logs: Firewall logs should be reviewed on a frequent basis to detect any security breaches. Firewall logs can reveal important details regarding network traffic patterns and security issues. Regularly monitoring firewall logs may aid in the identification of possible security breaches, allowing security professionals to take necessary action to secure the network.
Organizations can ensure that their firewalls are correctly set and effective in safeguarding their networks from security threats by following these recommended practices.
Conclusion
Firewalls play an important role in network security because they serve as the first line of defense against cyber threats. They are available in a variety of forms and filtering methods to meet the individual demands of a network or a host computer.
Firewall rules enable or deny particular types of traffic depending on parameters such as port numbers, IP addresses, protocols, and applications. Firewall rules are required to ensure that the firewall provides the greatest possible protection against cyber-attacks. To ensure that the firewall provides the greatest possible protection against new and emerging threats, it must be updated and maintained on a regular basis.
Finally, firewalls are a critical component of network security. They serve as a first line of defence against cyber threats and come in a variety of forms and filtering methods to meet the individual demands of a network or a host machine.
Firewall rules enable or deny particular types of traffic depending on parameters such as port numbers, IP addresses, protocols, and applications. To ensure that the firewall provides the greatest possible protection against new and emerging threats, it must be updated and maintained on a regular basis.
You can also read our articles.
Examining the Surprising Impact of Disconnecting from the Internet on Society